Using HTTP Redirect binding in OpenSAML 4
This article discusses singing and sending in OpenSAML 4. If you're looking for an article on OpenSAML 3, you will find it here and if you're looking for an article on OpenSAML 2, you will find it here
SAML messages can be sent using different methods, called bindings. There are four main standard bindings being used today, HTTP Redirect, HTTP POST, HTTP Artifact and SOAP.
This tutorial will walk you through how to send a message, specifically a authentication request, using HTTP Redirect in OpenSAML.
The HTTP Redirect binding
The Redirect binding uses the function of HTTP Redirects the transport messages between SP and IdP with the use of the user browser.
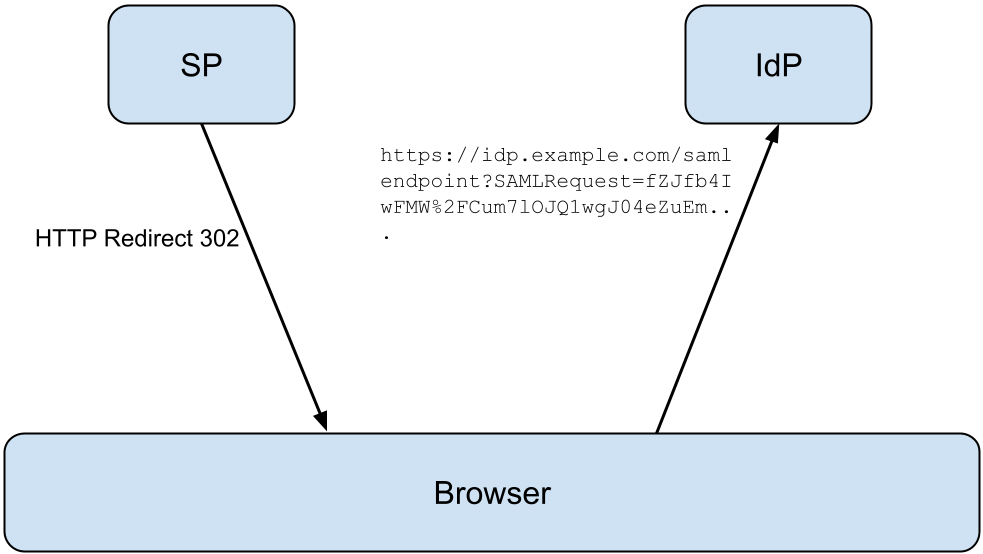
- When the SP or IdP want to send a message it responds to the current user with a HTTP Redirect to the receiver, with the encoded message in an URL parameter.
- When the browser receives the redirect, it redirects the user to the receiver.
- When the user arrives at the receiver of the message, the receiver will pick the message from the URL parameter and parses the message.
URL parameters explained
A typical redirect URL can look like this.
1http://localhost:8080/opensaml-http-redirect/receiverPage?SAMLRequest=fZJNb9swDIb%2FiqC744%2FagSvEKbwGxQJ0Q9C6PewyqDJdC5AlT6TT9t9PzsfQ9ZCLAIqv%2BFIPubp5Hwzbg0ftbMXTRcIZWOVabV8r%2FtTcRSW%2FWa9QDiYbRT1Rbx%2FgzwRILDy0KI6Zik%2FeCidRo7ByABSkxGP9415ki0SM3pFTznBWI4KnYHXrLE4D%2BEfwe63g6eG%2B4k0PDHs3mZa9AKMQgW1Hpy2FQNI550Fp2B8FHnAyxFx3iGRoDyxpJWcLzjahTW0PQcV7olHEsXFKmt4hiTIpk9iNYOcvRHM68tDqUJ7icIAOVHbyFTjbbir%2BW0nVdUVbpGVxnVxflV3X5UVxVaqlass0nWWIE2wtkrRU8SzJ0ihNonTZpLnIl6LIFlme%2F%2BJsd8LxTdsj5kvsXo4iFN%2BbZhfVAV4nFXH2fB5ZEPHTgMShA%2F95MpeLy%2FM4%2BLrpNX6hjwF%2FqDYTpY9tu4o%2Fm%2FzbiZ%2Bh6nazc0arD1Yb495uPUiCipOfApU75wdJl%2FuYb3QbdQepIC8t6mDL4%2FXJ9P%2FVW%2F8F&RelayState=teststateThere are four URL parameters used in the binding
- SAMLRequest/SAMResponse - The encoded, unsigned message
- RelayState - The relaystate, sent in the original request and send back in the response
- SigAlg - The algorithm used for signing
- Signature - Calculated signature
The authentication request is often the first message send when authenticating a user user SAML. This is true when the recommended approach of SP initiated SSO is used and the SP is the one that requests a user to be authenticated by the IdP.
Sending a message using OpenSAML 4
Creating message contexts to set the message, relaystate and receiving endpoint.
1MessageContext context = new MessageContext();
2context.setMessage(authnRequest);
3
4SAMLBindingContext bindingContext = context.getSubcontext(SAMLBindingContext.class, true);
5bindingContext.setRelayState("teststate");
6
7SAMLPeerEntityContext peerEntityContext = context.getSubcontext(SAMLPeerEntityContext.class, true);
8SAMLEndpointContext endpointContext = peerEntityContext.getSubcontext(SAMLEndpointContext.class, true);
9endpointContext.setEndpoint(URLToEndpoint(MESSAGE_RECEIVER_ENDPOINT));Creating, initializing and sending the message using HTTPRedirectDeflateEncoder.
1HTTPRedirectDeflateEncoder encoder = new HTTPRedirectDeflateEncoder();
2encoder.setMessageContext(context);
3encoder.setHttpServletResponse(httpServletResponse);
4
5encoder.initialize();
6encoder.encode();Receiving a message using OpenSAML 4
Using HTTPRedirectDeflateDecoder to decode the received message from the HTTPServletRequest
1HTTPRedirectDeflateDecoder decoder = new HTTPRedirectDeflateDecoder();
2decoder.setHttpServletRequest(req);
3
4decoder.initialize();
5decoder.decode();
6MessageContext messageContext = decoder.getMessageContext();
7authnRequest = (AuthnRequest) messageContext.getMessage();Get it on Github!
The full running sample is availible on Github at https://github.com/rasmusson/OpenSAML-sample-code under opensaml-http-redirect
Just clone it, run it, go nuts!
1git clone https://github.com/rasmusson/OpenSAML-sample-code/
2cd opensaml-http-redirect
3mvn tomcat:runAll messages are printed in the console
Browse to http://localhost:8080/opensaml-http-redirect/redirectPage
Summary
In this post we have looked on.
- The basics of the HTTP redirect binding
- Sending a message using OpenSAML 4,
- Receiving a message using OpenSAML 4
